笔记本电脑
连接显示屏后,官方截图有拉伸
- 使用shareX截屏软件,它的截屏可以解决显示屏比例不对等的问题。
电脑蓝屏,报错:system_thread_exception_not_handled
-
- 按 Win+R 输入
eventvwr.msc,打开事件查看器。导航到“Windows 日志” > “系统”,查看蓝屏发生时的错误详情。计算机已经从检测错误后重新启动。检测错误: 0x0000007e (0xffffffffc0000005, 0xfffff80075ee24da, 0xfffff50949215f88, 0xfffff509492157a0)。已将转储的数据保存在: C:\windows\Minidump\120224-13984-01.dmp。报告 ID: 7b793d86-ae00-4ef6-be9a-4b5653791bda。
- 按 Win+R 输入
- 下载 WinDbg Preview,点击“File” > “Open Dump File”,选择转储文件
C:\Windows\Minidumsystem_thread_exception_not_handledp\120224-13984-01.dmp显示
``` SYSTEM_THREAD_EXCEPTION_NOT_HANDLED (7e) This is a very common BugCheck. Usually the exception address pinpoints the driver/function that caused the problem. Always note this address as well as the link date of the driver/image that contains this address. Arguments: Arg1: ffffffffc0000005, The exception code that was not handled Arg2: fffff80075ee24da, The address that the exception occurred at Arg3: fffff50949215f88, Exception Record Address Arg4: fffff509492157a0, Context Record Address Debugging Details:
KEY_VALUES_STRING: 1
Key : AV.Fault
Value: Write
Key : Analysis.CPU.mSec
Value: 484
Key : Analysis.Elapsed.mSec
Value: 13226
Key : Analysis.IO.Other.Mb
Value: 3
Key : Analysis.IO.Read.Mb
Value: 1
Key : Analysis.IO.Write.Mb
Value: 7
Key : Analysis.Init.CPU.mSec
Value: 93
Key : Analysis.Init.Elapsed.mSec
Value: 18045
Key : Analysis.Memory.CommitPeak.Mb
Value: 109
Key : Analysis.Version.DbgEng
Value: 10.0.27725.1000
Key : Analysis.Version.Description
Value: 10.2408.27.01 amd64fre
Key : Analysis.Version.Ext
Value: 1.2408.27.1
Key : Bugcheck.Code.LegacyAPI
Value: 0x1000007e
Key : Bugcheck.Code.TargetModel
Value: 0x1000007e
Key : Dump.Attributes.AsUlong
Value: 1008
Key : Dump.Attributes.DiagDataWrittenToHeader
Value: 1
Key : Dump.Attributes.ErrorCode
Value: 0
Key : Dump.Attributes.KernelGeneratedTriageDump
Value: 1
Key : Dump.Attributes.LastLine
Value: Dump completed successfully.
Key : Dump.Attributes.ProgressPercentage
Value: 0
Key : Failure.Bucket
Value: AV_nt!RtlClearBitsEx
Key : Failure.Hash
Value: {2f161bcd-eef7-a5da-06f3-04818da144fe}
BUGCHECK_CODE: 7e
BUGCHECK_P1: ffffffffc0000005
BUGCHECK_P2: fffff80639ae24da
BUGCHECK_P3: fffff987c45b4f88
BUGCHECK_P4: fffff987c45b47a0
FILE_IN_CAB: 120624-15781-01.dmp
DUMP_FILE_ATTRIBUTES: 0x1008 Kernel Generated Triage Dump
FAULTING_THREAD: ffffe681ca998080
EXCEPTION_RECORD: fffff987c45b4f88 – (.exr 0xfffff987c45b4f88) ExceptionAddress: fffff80639ae24da (nt!RtlClearBitsEx+0x000000000000004a) ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 0000000000000001 Parameter[1]: ffffafb440426308 Attempt to write to address ffffafb440426308
CONTEXT: fffff987c45b47a0 – (.cxr 0xfffff987c45b47a0)
rax=00000000000000fd rbx=0000000002130000 rcx=0000000000000001
rdx=0000000000000001 rsi=ffffafb440426308 rdi=0000000000000001
rip=fffff80639ae24da rsp=fffff987c45b51c0 rbp=0000000000007658
r8=0000000000000001 r9=ffffe681ff0b92c0 r10=0000000000000000
r11=0000000000000000 r12=ffffe681ff0b92c0 r13=0000000000000000
r14=fffff80639800000 r15=fffff987c45b5290
iopl=0 nv up ei pl nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00050202
nt!RtlClearBitsEx+0x4a:
fffff80639ae24da 2006 and byte ptr [rsi],al ds:002b:ffffafb440426308=??
Resetting default scope
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: OverlayHelper.
WRITE_ADDRESS: fffff8063a51d470: Unable to get MiVisibleState Unable to get NonPagedPoolStart Unable to get NonPagedPoolEnd Unable to get PagedPoolStart Unable to get PagedPoolEnd unable to get nt!MmSpecialPagesInUse ffffafb440426308
ERROR_CODE: (NTSTATUS) 0xc0000005 - 0x%p 0x%p %s
EXCEPTION_CODE_STR: c0000005
EXCEPTION_PARAMETER1: 0000000000000001
EXCEPTION_PARAMETER2: ffffafb440426308
EXCEPTION_STR: 0xc0000005
STACK_TEXT:
fffff987c45b51c0 fffff80639a576f0 : 0000000002130000 0000000000001841 0000000000001841 0000000000000000 : nt!RtlClearBitsEx+0x4a
fffff987c45b51f0 fffff80639a575fd : ffffe681ff0b92c0 ffffe681ca998080 0000000002131841 fffff80639a1c449 : nt!MiClearVadCellBits+0xa0
fffff987c45b5240 fffff80639a572e0 : ffffe68100000000 ffffe681ff0b9bd0 ffffe681ff0b92c0 ffffe681cfdf6550 : nt!MiClearVadBits+0xcd
fffff987c45b5290 fffff80639eb05d6 : 0000000000000000 0000000000000001 0000000000000000 0000000000000000 : nt!MiRemoveVad+0x2c0
fffff987c45b5340 fffff80639b1989f : 0000021318410000 0000000000000000 ffffe681cfdf6080 0000000000000000 : nt!MiDeleteVad+0x336
fffff987c45b5400 fffff80639f969ed : 0000000000000000 0000000000000000 fffff987c45b5560 fffff98700000000 : nt!MiFreeVadRange+0xa3
fffff987c45b5460 fffff80639f96605 : 0000000000000000 fffff80639f2c31d 0000000000000002 0000000000000000 : nt!MmFreeVirtualMemory+0x3ad
fffff987c45b55a0 fffff80639c2a605 : ffffe681ca998080 ffffe681ef7e5000 0000000000000020 ffffe681e8ca9308 : nt!NtFreeVirtualMemory+0x95
fffff987c45b5600 fffff80639c1aa90 : fffff8063a1ec2c2 0000000000000000 fffff80639f2c31d 0000000000000010 : nt!KiSystemServiceCopyEnd+0x25
fffff987c45b5798 fffff8063a1ec2c2 : 0000000000000000 fffff80639f2c31d 0000000000000010 0000000000050246 : nt!KiServiceLinkage
fffff987c45b57a0 fffff80639f2c370 : ffffe681e8ca92f0 000000000000ff18 0000021318410000 ffffe681e8ca9308 : nt!EtwpFreeUserBufferSpace+0x76
fffff987c45b57d0 fffff80639f2c11c : 0000000000000000 fffff80639a35d13 0000000200000000 fffff80600000000 : nt!EtwpRealtimeInjectEtwBuffer+0x170
fffff987c45b5880 fffff80639f592d8 : fffff987c45b5900 ffffe681ef7e5000 0000000000000000 ffffe681df3b39c0 : nt!EtwpRealtimeDeliverBuffer+0x7c
fffff987c45b58e0 fffff80639f593a2 : ffffe681df3b39c0 00000000c0000001 ffffe681df3b39c0 0000000000000002 : nt!EtwpFlushBufferToRealtime+0x34
fffff987c45b5910 fffff80639f59a66 : 0000000000000000 0000000000000000 ffffe681df3b39c0 ffffe681ef7e5000 : nt!EtwpFlushBuffer+0x5a
fffff987c45b5940 fffff80639f58f91 : ffffe681df3b39c0 ffffe681df3b39c0 ffffe681df3b3ba0 ffffe681df3b3b88 : nt!EtwpFlushActiveBuffers+0x22a
fffff987c45b5ab0 fffff80639b4d4d7 : fffffffffffffffd ffffe681ca998080 0000000000000080 fffff80639f58dd0 : nt!EtwpLogger+0x1c1
fffff987c45b5b30 fffff80639c1a114 : ffff86817d993180 ffffe681ca998080 fffff80639b4d480 0000000000000246 : nt!PspSystemThreadStartup+0x57
fffff987c45b5b80 0000000000000000 : fffff987c45b6000 fffff987c45af000 0000000000000000 0000000000000000 : nt!KiStartSystemThread+0x34
SYMBOL_NAME: nt!RtlClearBitsEx+4a
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.22621.4455
STACK_COMMAND: .cxr 0xfffff987c45b47a0 ; kb
BUCKET_ID_FUNC_OFFSET: 4a
FAILURE_BUCKET_ID: AV_nt!RtlClearBitsEx
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {2f161bcd-eef7-a5da-06f3-04818da144fe}
Followup: MachineOwner
### 电脑蓝屏终止代码:PAGE_FAULT_IN_NONPAGED_AREA
+ 情况:使用微信打视频电话的时候蓝屏,可能之前开了很多VScode
### 电脑蓝屏代码:DRIVER_VERIFIER_DETECTED_VIOLATION
+ 蓝屏后重启遇到系统更新,再次进入使用惠普助手检查驱动更新报错
#### 显示
Debugging Details: ——————
*** WARNING: Unable to verify timestamp for aswArPot.sys
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 781
Key : Analysis.Elapsed.mSec
Value: 32956
Key : Analysis.IO.Other.Mb
Value: 0
Key : Analysis.IO.Read.Mb
Value: 1
Key : Analysis.IO.Write.Mb
Value: 0
Key : Analysis.Init.CPU.mSec
Value: 796
Key : Analysis.Init.Elapsed.mSec
Value: 23110
Key : Analysis.Memory.CommitPeak.Mb
Value: 88
Key : Analysis.Version.DbgEng
Value: 10.0.27725.1000
Key : Analysis.Version.Description
Value: 10.2408.27.01 amd64fre
Key : Analysis.Version.Ext
Value: 1.2408.27.1
Key : Bugcheck.Code.LegacyAPI
Value: 0xc4
Key : Bugcheck.Code.TargetModel
Value: 0xc4
Key : Dump.Attributes.AsUlong
Value: 1008
Key : Dump.Attributes.DiagDataWrittenToHeader
Value: 1
Key : Dump.Attributes.ErrorCode
Value: 0
Key : Dump.Attributes.KernelGeneratedTriageDump
Value: 1
Key : Dump.Attributes.LastLine
Value: Dump completed successfully.
Key : Dump.Attributes.ProgressPercentage
Value: 0
Key : Failure.Bucket
Value: 0xc4_f6_aswArPot!unknown_function
Key : Failure.Hash
Value: {e72fd478-aa81-5cc0-f962-3cf420a400ba}
BUGCHECK_CODE: c4
BUGCHECK_P1: f6
BUGCHECK_P2: 1c74
BUGCHECK_P3: ffff8183836960c0
BUGCHECK_P4: fffff8047acc6c10
FILE_IN_CAB: 121324-28484-01.dmp
DUMP_FILE_ATTRIBUTES: 0x1008 Kernel Generated Triage Dump
FAULTING_THREAD: ffff81837aa49080
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: msedge.exe
STACK_TEXT:
ffffc2007f3dc438 fffff802365d6b0b : 00000000000000c4 00000000000000f6 0000000000001c74 ffff8183836960c0 : nt!KeBugCheckEx
ffffc2007f3dc440 fffff802365d5747 : 0000000000000000 fffff80236436930 fffff80236436930 0000000000000000 : nt!CarInitiateBugcheck+0x47
ffffc2007f3dc480 fffff80236acd34c : 00000000000000c4 0000000000000000 0000000000000004 0000000000001c01 : nt!CarReportRuleViolationForTriage+0x147
ffffc2007f3dc500 fffff80236ad3e7f : 0000000000000002 ffff81837d9f30c0 fffff8047acc6c00 ffff8183836960c0 : nt!VerifierBugCheckIfAppropriate+0xc8
ffffc2007f3dc5a0 fffff8023689f03a : 0000000000000000 0000000000000000 ffffc2007f3dc7f0 ffff818366ab81c0 : nt!VfCheckUserHandle+0x19b
ffffc2007f3dc690 fffff802366cc45e : ffff8183836960c0 fffff80200000000 0000000000000000 0000000000001c00 : nt!ObpReferenceObjectByHandleWithTag+0x1d2bca
ffffc2007f3dc720 fffff802365e9989 : 00007fff5bff0e30 fffff802376e3ccb 00007fff5bff0e30 000000a7bcffdc18 : nt!ObReferenceObjectByHandle+0x2e
ffffc2007f3dc770 fffff8047acc6c10 : 000000a7bcffdcf0 000000a7bcffdca8 ffffc2007f3dc9c8 000000a7bcffdeb0 : nt!DifObReferenceObjectByHandleWrapper+0x109
ffffc2007f3dc820 000000a7bcffdcf0 : 000000a7bcffdca8 ffffc2007f3dc9c8 000000a7bcffdeb0 ffffc2007f3dc858 : aswArPot+0x16c10
ffffc2007f3dc828 000000a7bcffdca8 : ffffc2007f3dc9c8 000000a7bcffdeb0 ffffc2007f3dc858 0000000000000000 : 0x000000a7bcffdcf0
ffffc2007f3dc830 ffffc2007f3dc9c8 : 000000a7bcffdeb0 ffffc2007f3dc858 0000000000000000 00007fff00000000 : 0x000000a7bcffdca8
ffffc2007f3dc838 000000a7bcffdeb0 : ffffc2007f3dc858 0000000000000000 00007fff00000000 0000000000000080 : 0xffffc2007f3dc9c8
ffffc2007f3dc840 ffffc2007f3dc858 : 0000000000000000 00007fff00000000 0000000000000080 00000000002e002c : 0x000000a7bcffdeb0
ffffc2007f3dc848 0000000000000000 : 00007fff00000000 0000000000000080 00000000002e002c fffff8047acdb930 : 0xffffc200`7f3dc858
SYMBOL_NAME: aswArPot+16c10
MODULE_NAME: aswArPot
IMAGE_NAME: aswArPot.sys
STACK_COMMAND: .process /r /p 0xffff8183836960c0; .thread 0xffff81837aa49080 ; kb
BUCKET_ID_FUNC_OFFSET: 16c10
FAILURE_BUCKET_ID: 0xc4_f6_aswArPot!unknown_function
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {e72fd478-aa81-5cc0-f962-3cf420a400ba}
Followup: MachineOwner
+ 在卸载了avast free antivirus之后,蓝屏暂时没有出现过。
### Dtsapo4service.exe占用CPU过高
+ https://candid.technology/dtsapo4service-high-memory-usage-fix/
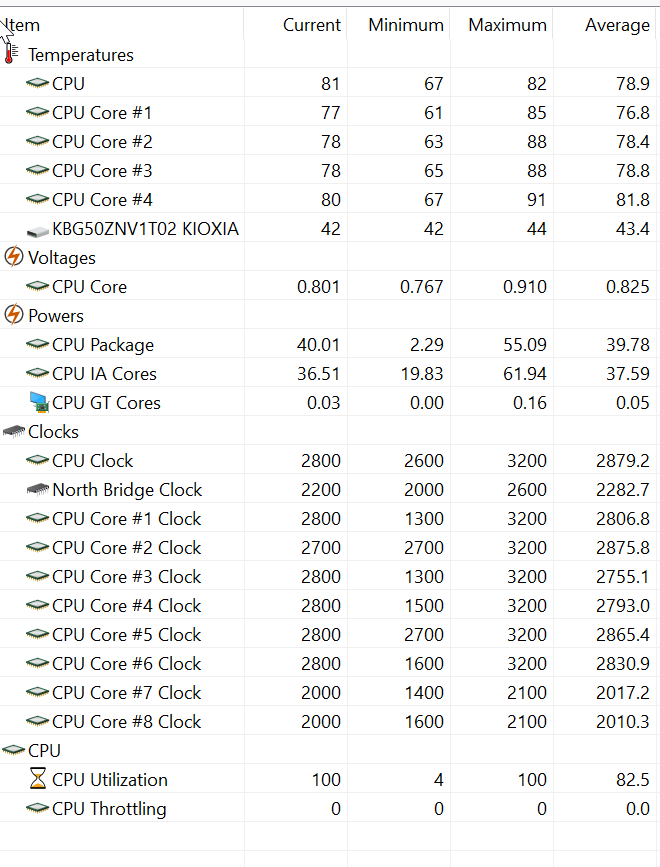
### aida64 烤结果
### 报错 ACE base.sys
确定了开机卡顿原因:
+ 之前问了GPT怎么解决蓝屏代码,他推荐了一种方案,要用系统的verifier
2. 利用Driver Verifier针对性验证
使用Windows自带的Driver Verifier工具来针对有问题的驱动进行验证是一个有条理的方法。
步骤如下:
打开管理员权限的CMD或PowerShell输入:
verifier /standard /driver <特定驱动名或通配符>
你可以针对某几个可疑驱动(如 aswArPot.sys, aswSP.sys, aswbidsdriver.sys, SdpNetFilter0.sys, AxUsbEth.sys, ace-game.sys等)启用。
+ 使用了之后发现一直卡卡的,偶然报错时GPT给了一种解决方法:
禁用驱动程序验证器
如果你在开发或测试中启用了驱动程序验证器,可以尝试禁用它:
- 以管理员身份打开 命令提示符。
- 输入以下命令:
verifier /reset - 按 Enter。
- 重启电脑。 ```
PS和PR下载和激活(建议支持正版)
参考b站视频
- 下载Adobe CC GenP v3.6.8.
- 下载好Adobe CC注册好 打开GenP(建议管理员模式运行),search后进行patch
- 重新打开Adobe CC,下载需要的软件
- 等待软件下载完毕后,再次打开GenP,search后进行patch
- 重新打开软件,即可正常使用
This line appears after every note.